Introduction to DKIM
DomainKeys Identified Mail or DKIM is a standard for signing email messages so that the recipient can verify the sender's email address. This allows recipient mail servers to detect sender address forgery, which is often used by spammers to avoid sender domain blacklists. Signing is done with a private key on the senders server, which matches a public key added to in the sender's DNS domain. The recipient can lookup this key at the domain in the From address, and use it to ensure that the email signature was created using the corresponding private key, which proves that the message was really sent from that domain.
Generate a DKIM Core Key. Enter the domain you'd like to generate keys for, for example dkimcore.org and hit the button. This online wizard is fine for generating keys for testing and evaluation. If you decide to use DKIM Core in production, though, you might want to consider the security risks.
Virtualmin uses a milter to implement DKIM signing and verification. This is background process that the Postfix or Sendmail mail server sends messages to for modification before they are sent to their final destination. Any email relayed through the Virtualmin system (either from a web-based mail read or a client like Outlook or Thunderbird) will have a signature added by the DKIM milter, as long as it is from a domain for which DKIM is enabled.
Only Virtualmin versions 3.81 and later support DKIM.
Installing DKIM Packages
Virtualmin supports the configuration of DKIM on Debian, Ubuntu, Fedora, CentOS and Redhat Enterprise systems, as these distributions provide the required DKIM milter package. The simplest way to install this is as follows :
- Login to Virtualmin as
rootand go to Email Messages -> *DomainKeys Identified Mail**. - Assuming that the required packages are not installed already, Virtualmin will display an error message about the missing configuration DKIM file. Click the Install Now button to have the appropriate package downloaded and installed.
Installation can also be done from the command line. Essl etimetrack license key generator. On Debian or Ubuntu, the command is :
apt-get install dkim-filter
while on CentOS, Fedora or Redhat Enterprise you will need to run :
yum install dkim-milter
Enabling DKIM in Virtualmin
To enable DKIM signing of outgoing email messages, follow these steps :
- Login to Virutalmin as
rootand go to Email Messages -> DomainKeys Identified Mail - Change Signing of outgoing mail enabled? to Yes.
- In the Selector for DKIM record name field enter a short name that you will use to identify the signing key. This is typically just the current year, like
2018. - Click the Save button.
Assuming all goes well, Virtualmin will report the steps taken to configure and enable DKIM.
Ssh generate key pair. Adding the Key to SSH Agentssh-agent is a program that can hold a user's private key, so that the private key passphrase only needs to be supplied once.
Only virtual servers that have both the DNS and email features enabled will have DKIM activated, as the mail server needs to be setup to use a private signing key whose corresponding public key is added to DNS.
By default, Virtualmin will also configure the DKIM milter to verify incoming email that has the proper signatures. DKIM-signed messages where the signature is incorrect or cannot be checked with a DNS lookup will be bounced or delayed. If you want to disable verification, set the Verify DKIM signatures on incoming email? option to No.
To turn off DKIM signing completely, just do the following :
- Login to Virutalmin as
rootand go to Email Messages -> DomainKeys Identified Mail - Change Signing of outgoing mail enabled? to No.
- Click Save.
This will remove the public key from all domains, and stop your mail server from signing messages with the DKIM milter.
DKIM (DomainKeys Identified Mail) is a method of signing electronic emails using public-private key. DKIM is used by receiving mail server for identifying email, that they are sent by authorized mail servers. It also minimizes the possibility of getting emails SPAM.
This tutorial will provide you a quick and easy way to set up DomainKeys with your POSTFIX running on CentOS and RHEL systems.
How DKIM Works ?
When we configured DKIM on sending servers. First, we generated a public/private key pair for signing outgoing messages. The public key is configured as TXT record on a domains name server, and the private key is configured in the outbound email server. When an email is sent by an authorized user of the email server, the server uses the stored private key to generate a digital signature of the message, which is inserted in the message as a header, and the email is sent as normal.
Step 1 – Install DKIM-milter
First make sure you have enabled EPEL repository in your system. After that install dkim-milter package using following command.
Step 2 – Generate Key Pair
Now create DKIM key pair using dkim-genkey command line utility provided by dkim-milter package. For this tutorial we are using domain name “example.com”, Change this name with your actual names.
Above command will generate two files default.private and default.txt. You can created multiple DKIM keys for different-2 domains and configure with your postfix server.
Now set the proper permissions on Keys directory.
Step 3 – Configure OpenDKIM
Edit the Opendkim configuration file and Add/Update following entries in file.
Then edit the domain keys lists setting file /etc/opendkim/KeyTable and add following entry.

Dkim Key Format
After that edit /etc/opendkim/SigningTable file and update following entry.
And edit /etc/opendkim/TrustedHosts file and update following entry.
Step 4 – Configure Postfix
Now edit POSTFIX configuration file /etc/postfix/main.cf and add following values at the end of file
Generate Dkim Key Exim Centos Server
finally start DKIM service using following command
Step 5 – Configure DNS Entry
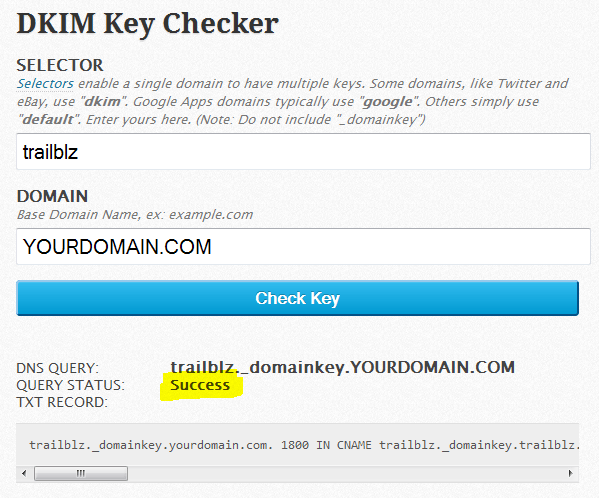
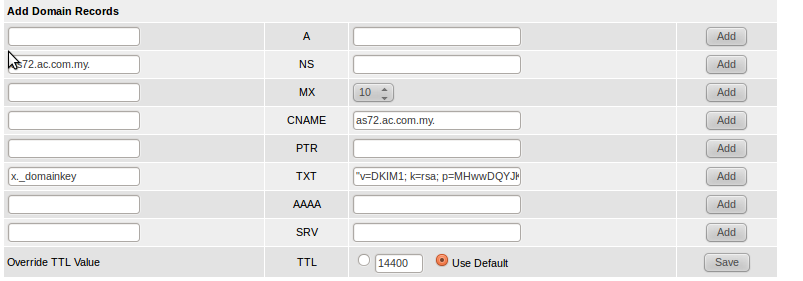
After configuring private key in postfix server. there will be another file /etc/opendkim/keys/example.com/default.txt/strong> generated by opendkim-genkey. Edit your DNS zone file and add this as TXT record found in default.txt. In my case this is like below.
Generate Dkim Key Exim Centos Server
Step 6 – Verify DKIM
To verify that DKIM is working properly. Let’s send a test email through command line
In the received email in our mailbox, open the source of the email and search for 'DKIM-Signature'. You will find something like below